1. All In One¶
All in one deployment can be done by preinstalling OCP in the CICD pipeline.
1.1. Prerequisite¶
System preinstalled with RHCOS
1.2. CICD¶
This phase should install a deployment system with OCP using the etcd patch
oc patch etcd cluster -p='{"spec": {"unsupportedConfigOverrides": {"useUnsupportedUnsafeNonHANonProductionUnstableEtcd": true}}}' --type=merge --kubeconfig /etc/kubernetes/kubeconfig
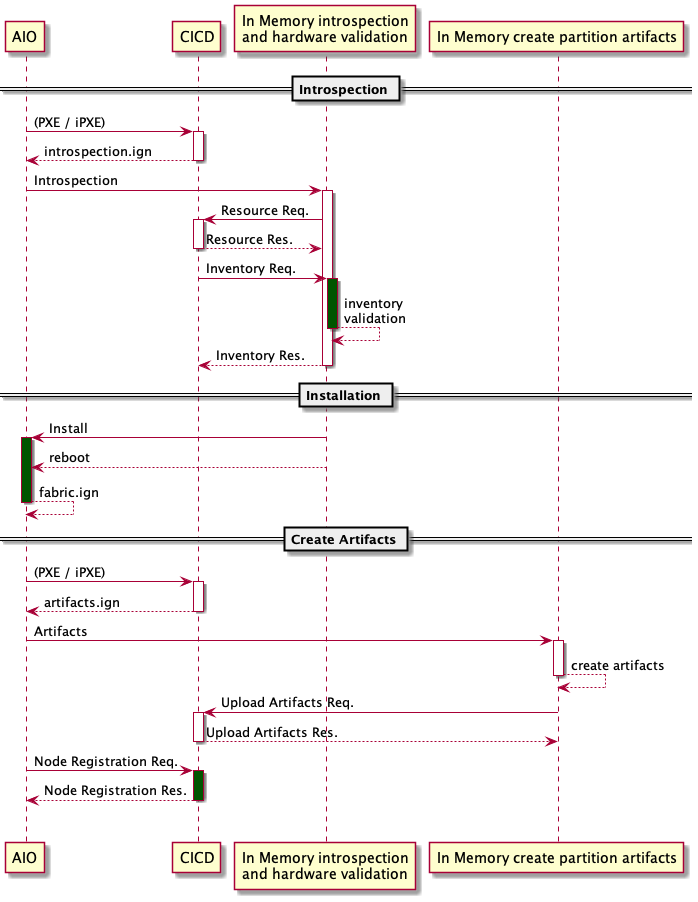
Deploy the static containers
Backup the partition standard images
# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
loop0 7:0 0 23.5G 0 loop /run/ephemeral
loop1 7:1 0 737.7M 0 loop /sysroot
sda 8:0 0 931.5G 0 disk
|-sda1 8:1 0 384M 0 part
|-sda2 8:2 0 127M 0 part
|-sda3 8:3 0 1M 0 part
`-sda4 8:4 0 931G 0 part
`-luksrecoverytarget 253:0 0 931G 0 crypt /var/mnt/recoverytarget
Backup boot and efi partitions
dd if=/dev/sda1 of=boot.raw bs=512
dd if=/dev/sda2 of=efi.raw bs=512
Backup the root partition (device could be sdX or nvme0X or vdaX, which will be detected and determined during the introspection phase)
archive_rootfs() {
rootfs="$1"
echo "Open rootfs partition"
echo "" | cryptsetup open /dev/${rootfs} luksrecoverytarget --type luks
mkdir -p /mnt/recoverytarget
mount /dev/mapper/luksrecoverytarget /mnt/recoverytarget
# Archive the rootfs
tar --acls --xattrs -cpvfz /home/core/rootfs.tar.gz -C /mnt/recoverytarget . &
# umount /var/mnt/recoverytarget
# cryptsetup close luksrecoverytarget
}
Note
The partition size might be different, so dd might not be feasible for large partitions.
1.3. Deployment¶
The deployment is done via an ignition file that will start the “aio” deployment service in memory which will fetch the partition images from an infrastructure deployment service and write them on the disk. Apply site customizations and finally, update the grub as the installed backup might contain a new kernel.
1.3.1. Example¶
curl -o boot.raw https://artifacts.stroila.ca/boot.raw
curl -o efi.raw https://artifacts.stroila.ca/efi.raw
curl -o rootfs.tar.gz https://artifacts.stroila.ca/rootfs.tar.gz
Write/create the rhcos partitions
dd if=boot.raw of=/dev/sda1 bs=512
dd if=efi.raw of=/dev/sda2 bs=512
Create rootfs partition and format using luksFormat
Check the luks partition
# cryptsetup luksDump /dev/sda4
LUKS header information
Version: 2
Epoch: 5
Metadata area: 16384 [bytes]
Keyslots area: 16744448 [bytes]
UUID: 00000000-0000-4000-a000-000000000002
Label: crypt_rootfs
Subsystem: (no subsystem)
Flags: (no flags)
Data segments:
0: crypt
offset: 16777216 [bytes]
length: (whole device)
cipher: cipher_null-ecb
sector: 512 [bytes]
Keyslots:
0: luks2
Key: 256 bits
Priority: normal
Cipher: cipher_null-ecb
Cipher key: 256 bits
PBKDF: argon2i
Time cost: 4
Memory: 452702
Threads: 1
Salt: 55 5c c2 50 b8 3b ce c1 57 dd f0 17 b0 59 cd 58
a5 0f 6f fe 2b 4f 5b 32 1e fe ec b0 ea a1 b3 40
AF stripes: 4000
AF hash: sha256
Area offset:32768 [bytes]
Area length:131072 [bytes]
Digest ID: 0
Tokens:
9: coreos
Keyslot: 0
Digests:
0: pbkdf2
Hash: sha256
Iterations: 239619
Salt: 38 f8 18 f1 d6 b0 e5 1e 21 5a 54 dc d5 54 16 55
55 06 02 41 a5 1b 57 cd f9 52 4a 0d 5b 14 7a 50
Digest: 85 f9 37 96 b6 77 4a cb 02 88 a1 8b 5e 4c a0 34
04 9b 5b ff ce ba 34 83 4b 6f 8c 02 e0 3b 1d c5
Additional customasations can be accomplished by aio service mounting the partitions and update as necessary
1.3.2. Example¶
Mount the rhcos install partitions
mkdir -p /mnt/rhcos /mnt/rootfs
mount -t ext4 /dev/sda1 /mnt/rhcos
mount /dev/sda2 /mnt/rhcos/efi
echo "" | cryptsetup open /dev/sda4 luksrecoverytarget --type luks
mount /dev/mapper/luksrecoverytarget /mnt/rootfs
1.4. Build Out¶
Using a standard RHCOS system attached to a Vfabric staging where it will stage with the local environment image.
The system will join the basic fabric and request the ignition role from the API server
The OCP master needs to approuve the csr and let the new node join
Note
Special consideration should be consider when a master role is requested regarding the supported number of masters requirements fullfilment.